ADD ON: SSO (Single Sign-On)
Contact support@sessionboard.com to receive pricing for this add-on.
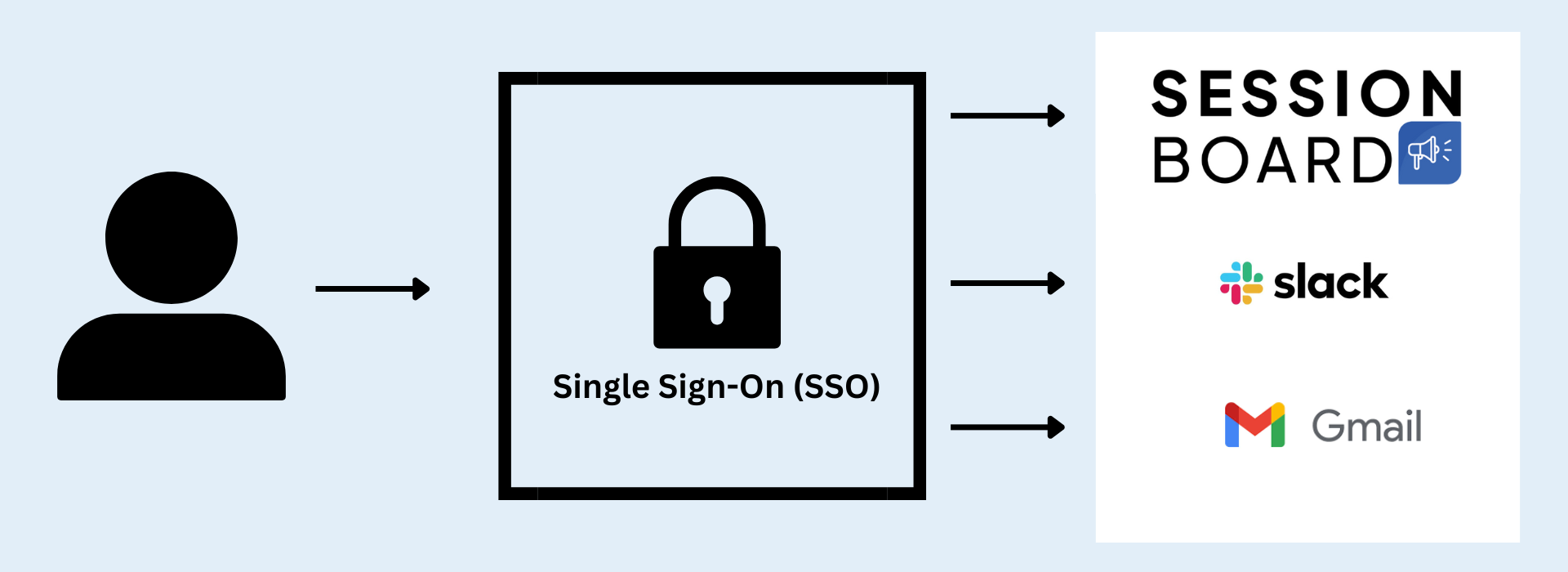
Single Sign-On (SSO) is an authentication process that allows users to access multiple applications or services with a single set of login credentials. Instead of having to remember and enter different usernames and passwords for each application, users log in once to a central authentication service and then gain access to all linked systems without needing to log in again.
Examples of SSO providers include: Okta, Auth0, and Microsoft Azure Active Directory (Azure AD), and many more!
Benefits of SSO-
Unified Access: Users can access multiple applications or services after logging in just once.
-
Improved Security: By reducing the number of passwords users need to remember and manage, SSO can lower the risk of weak or reused passwords. Centralized authentication also makes it easier to enforce strong security policies.
-
User Convenience: Simplifies the login process for users, leading to a smoother and more efficient experience.
-
Centralized Management: IT administrators can manage user access and permissions from a single point, streamlining administrative tasks and improving oversight.
-
Integration: SSO systems often integrate with various identity providers and applications, facilitating access across diverse platforms and services.
-
Sessionboard supports the following SSO configurations: SAML (Security Assertion Markup Language) & OIDC (OpenID Connect).
-
Sessionboard can set up a different SAML / OIDC configuration for the Session Submission Form, Portals, and Admin login.
-
Sessionboard does not support Two-factor authentication (2FA) at this time.
SAML Setup
SAML (Security Assertion Markup Language) is an open source standard for authentication. It allows an organization to use one set of credentials along multiple systems by exchanging information between IDP (Identity Providers) and SP (Service Providers).
Customer requirements:The customer must provide the following information to Sessionboard to enable SAML 2.0 SSO:
-
Identity Provider Name - A SAML application created in the vendor identity provider.
-
x509 Certificate
-
Issuer: Used to identify the provider’s application uniqueness
-
Domain: which domain is intended to support SSO).
- SSO URL
-
Test User: To confirm the login flow
Sessionboard will provide the following information to the customer:
-
Assertion Consumer Service URL: This is the url that receives a POST call from the identity provider with the SAML assertion. This endpoint will use the certificate to check that.
-
Issuer URL: This is an identifier of the SP.
By default, Sessionboard expects the following attributes to be returned as part of the user profile:
-
id: default ID from the SAML remote user directory.
-
firstName: user first name, used to reference the user and associated contact in our system
-
lastName: user last name, used to reference the user and associated contact in our system
-
email: user email that is used to log into Sessionboard and for authentication communications (password reset, new user invitation, etc.)
-
nameID: also user email
OIDC Setup
OIDC is a protocol created by the OpenID foundation and wraps OAuth2.0. OAuth2.0 is an authorization protocol while the ultimate goal of OIDC is authentication. It works using a flow of HTTP requests between the OIDC Provider and the Relaying Party.
The customer must provide the following information to Sessionboard to enable OIDC SSO:
-
Identity Provider Name
-
Domain: Optioinal, required if SSO is for Admin
- Authorization URL
-
Issuer
-
Token Url
-
User Info URL
-
Client ID
-
Client Secret:
- Scopes
Sessionboard will provide the following information to the customer:
- Callback URL
-
sub: default ID
-
given_name: Its the first name.
-
family_name: Its the last name.
-
preferred_username: email
If you are ready to set up SSO in your account please reach out to support@sessionboard.com and we will be happy to assist.
